 Steganos VPN Online Shield
Steganos VPN Online Shield
Absolute security and privacy. For all your devices - IT Security made in Germany.
Install and surf anonymously - it couldn't be easier. Quickly and easily preserve your digital freedom - because it's your right:
Don't let anyone spy on you and monitor and track your online behavior.
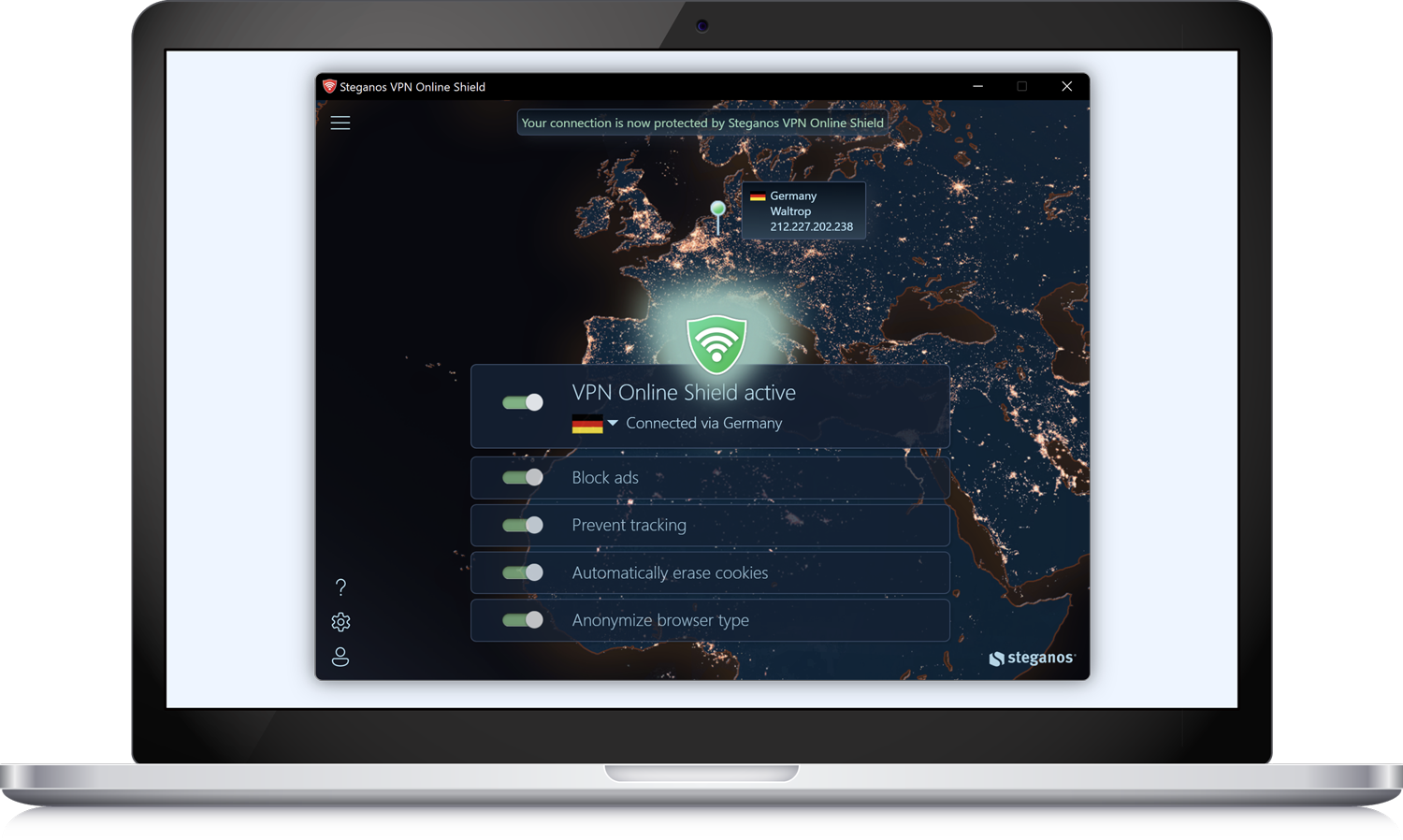
What is a VPN?
VPN stands for Virtual Private Network.
A VPN is a technology used to establish a secure connection over the Internet. It encrypts your Internet connection and routes your traffic through servers located in different locations around the world. This protects your online privacy by preventing third parties from tracking your internet activity.

Videos from all over the world
Surf free and uncensored! - Finally access blocked videos and websites worldwide. And yes, it's legal.
Surf without borders
Access your favorite websites even from abroad. Steganos VPN Online ShIeld automatically selects the best connection for you.
Secure WiFi everywhere
Your connection is encrypted with the highly secure 256-bit AES method - even in public hotspots.
Invisible on the net
It's your right: don't let anyone spy on you. Steganos VPN Online Shield hides your IP address.
Surf securely
Whether bank data or passwords - data theft is not okay! Steganos VPN Online Shield protects you while surfing the Internet.
Also for downloads
Unlike other programs, Steganos VPN Online Shield protects your IP address not only in the browser, but also for downloaders.
For every browser
No matter if you use Chrome, Firefox, Edge or something else entirely. Steganos VPN Online Shield works with any browser.
Server locations worldwide
Not all web content is available to all users worldwide. Choose your IP location from a pool of numerous server locations worldwide and bypass country blocks and censorship.What our customers say
RH
Robert H.

Very good product. Have used for years.

Very good product. Have used for years.
PS
P. Stewart

The internet speed is very fast with the vpn!

The internet speed is very fast with the vpn!
PM
Paula M.

Very easy to use. Works fine.

Very easy to use. Works fine.







